Proxmark3 community
Research, development and trades concerning the powerful Proxmark3 device.
Remember; sharing is caring. Bring something back to the community.
"Learn the tools of the trade the hard way." +Fravia
You are not logged in.
Announcement
Time changes and with it the technology
Proxmark3 @ discord
Users of this forum, please be aware that information stored on this site is not private.
#1 2009-08-21 04:21:29
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Help cloning my flat keys
Hello all!
I've got a bit of a problem, and i figured this might be a good place to ask for help..
I live in a block of flats which have a RFID entry system made by Urmet Domus. I have no idea what frequecy these RFID chips use or what the chip-type is... but i'll happily cut one up and have a look if it means a resolution to my problem. Hell, i'd even buy a proxmarkIII from proxmark3.com!
My problem is simple - when ever anyone in my block of flats looses there RFID fob, they get charged a *ridiculous* amount of money.
On two occasions mine have just suddenly stopped working on me, and i've been asked to pay £100 both times for a new one! In two years!!
If you want to get a fob which also opens the garage door (not RFID or infrared. Some other wireless method.) expect to pay a LOT more!
Seeing as RFID chips cost pennys to make, and a whole fob probibly costs under £3, i think we're all just being ripped off.
So - i figured i would help everyone in my block of flats out by making a fob cloner/writer.
But, alas, RFID isn't my forte. This is the first bit of low-level wireless security i've ever delt with (802.11 doesn't count!)
So I guess I have a few questions, and if anyone could answer any of them, i'm be deeply greatful!! :
1)
I'm a bit fuzzy on how to go about writing the chips. It's not like DVD-R and DVD-RW. It seems that most/all chips are writable - untill you fill them up. Some/most are even writable when they're in use.
So what i'm basically saying is, if for example the key fob i use to get into my apartment block turns out to be a very basic chip-type which can be read/sniffed/cloned on a proxmark easily - what am i going to need to write this onto a new chips for people?
I can't have people carrying proxmark3's around all the time, hehe, so i need to be able to write to inexpensive chips.
2)
Does Proxmark3 work with rfidiot? I didn't see it listed in the hardware of the getting started page...
I assume i will need rfidiot to get the data off the existing fobs ready to be cloned.(?)
3)
I think this would also be a perfect oppertunity to test out the security of my wireless entry system from Urmet Dormus.
If for example i found a predictable code assigned to each fob, i could use it to see if Urmet built a backdoor into there system. A keyfob which opens every installation for example, which hasn't been documented.
To do this i would need to read, manipulate, and replay data - abit like i would do with aireplay-ng.
Is all this possible with a Proxmark3?
If i ever do manage to make cheap fobs for people in my building, i would charge them very little (£10, presuming the cost per key was £5). Once i've made back the cost of the proxmark, i would give the rest of the money i made from then on to the Proxmark development team (if such a team still exists). It wouldn't be much... but i'm sure every little counts when it comes to hosting webservers! ![]()
So please - if you have any advice for me at all, i'd be very greatful to hear it!
All the best!
~ John
Offline
#2 2009-08-21 10:08:34
- djrevmoon
- Contributor
- Registered: 2008-06-23
- Posts: 13
Re: Help cloning my flat keys
you need to identify the type of card first. you dont need a proxmark to do that. Get a cheap (30 EUR or so) reader from somewhere that works with adam's tools (rfidiot). most likely you'll be able to determine the type of card with that.
when you know the type, its easy to figure out what can be done...... some can be freely copied, others not so easily.
Offline
#3 2009-08-21 12:43:34
- d18c7db
- Contributor
- Registered: 2008-08-19
- Posts: 292
Re: Help cloning my flat keys
Another option is to mail one of those key cards that "stopped working" to one of us here and we could investigate first hand what type of system it is, unless of course they make you return the dead one back after paying for a new one.
Offline
#4 2009-08-21 14:42:19
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Thanks for your time guys - i didn't expect replies so soon!
Unfortunatly i binned the fobs which stopped working awhile ago, ![]()
On the plus side, i still have three working fobs to play with!
I'll looking into getting a cheap reader now.. but... erm... I was under the impression that not only would i need to know if the chips use high frequency or low frequency, but i'd also need to make sure that the reader supports the protocol from the chip manufacturer.
In other words, i thought readers where very specific to their coresponding chips, and unless i bought some expensive broad-spectrum hardware like the Proxmark or URSP, etc, i would need to know the exact hardware type of these chips.
This is most-likely wrong. I've spent probibly no more than 4 hours total reading articles / watching videos on the internet about RFID.
Anyway, what i do know is that we can guess if it's high/low frequency by looking at the number of coils (read it here: Analyzing an unknown access control system) so i'll start with cracking a fob open and taking a look.
Cheers guys! I'll have an update with photos in a few minutes :3
Last edited by John (2009-08-24 13:18:28)
Offline
#5 2009-08-22 02:49:50
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Sorry it took so long to get a picture. Two of the fobs are sealed up in plastic molds, whilst the one my partner has is inside a plastic case which is un-screwable.
For this reason, i asked her to send me a photo of the RFID chip inside (she's at her perents for the weekend), instead of me cracking one of mine open with a knife.
She sent me back this crappy picture - 
If anyone could tell anything from that picture at all, i would be amazed -_-;
If you need a better picture, i'll crack one open tonight/tomorrow and take a 'proper' picture with my camera (and not her phone)
Offline
#6 2009-08-22 03:33:40
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Okay, so, seeing as there's nothing of value on the outside of the chip - which card reader (which works with RFIDiot) should i get?
There are plenty to choose from, but certain programs are dependant on the card reader...
Do some readers do both high and low frequencies, or am i going to need two?
Sorry guys - i'm sure once i've gotten a bit more into this i'll be able to search for the answers to these questions instead of ask. Just that right now i know so little it's hard to get an understanding of anything.
Ta!
Offline
#7 2009-08-22 04:03:40
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
The Omnikey 5321 seems to be pretty good, but i think it only does 13.56 MHz.
Would this be acceptible for discovering more about a totally unknown RFID fob, or should i try a different frequency first?
Offline
#8 2009-08-22 09:57:28
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
Hi John,
Did a search on your key fob and it definitely comes out to 125khz. I too am looking at ways to decode access tags which will enable me to copy the id onto another card.
The proxmark will tell you a lot about your tag if you choose to buy and it will definitely have an impact on your sex life- once it's in your hands! You should expect to spend hours in front of your monitor staring at glamorous repetitive waves that stretch along your screen, like legs of wonderwoman, while the matrix of naked 1s and 0's bouncing around in your head, screeming your name, are just begging to be released from the spell which was placed on them by the evil encryptor.
If your lucky, you will find that some functions on the proxmark will help you get your tag id.
Is this your fob on page 2??
Last edited by XEROEFFECT (2009-08-22 11:38:32)
Offline
#9 2009-08-22 14:35:14
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Hehe, wow!
I have looked everywhere for the frequency of these fobs. I scoured the website, called all the help lines, spent ours looking through google images for a fob like mine - never found a thing.
But you've clearly found the manufacturer!!
I have two of the 500's and my girlfriend (who took the car and needed the key which opened the garage gate) has the 999.
Because the 999 needs batteries for the 433Mhz transmitter, it could be unscrewed and opened up - hence why i asked her for a photo before cracking a 500 open and ruining it.
So! What do you think is the next step?
Buy a proxmark? From what i understand RFIDiot doesn't support it ( it's not on the list of devices ![]() )
)
Also, reading the tag is only half the battle - writing it onto a new tag may/may not be possible with any LF reader. I don't know ![]()
Anyway - thank you so much XEROEFFECT, d18c7db and djrevmoon!
At the least, i can ask the manufacturer directly for more tags (instead of paying £100 for one), and at best i can delve into the world of RFID ![]()
Offline
#10 2009-08-22 16:48:01
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
John,
Your access tag contains a unique ID which is programmed into the building access control server (computer). This server will grant your tag access depending on what parameters have been set through software i.e- the floor level you live on, recreational areas such as pool or tennis courts and parking facilities. Only the building manager will have administrator rights allowing him/her to change parameters. Buying the fobs direct from the manufacturer will not aid your situation unless you know the new fobs ID and could hack into the server. Don't waste your hard earned cash on dummy fobs. Extracting the ID from your tag will be a challenge in itself, but that dosn't mean it ends here. If you can't justify buying a proxmark3 and your stuck between a rock and a hard place, send your fob to one of the pros like d18c7db, metaphorically speaking, He really has his shit together ![]()
Offline
#11 2009-08-23 02:01:09
- henryk
- Contributor
- Registered: 2009-07-27
- Posts: 99
Re: Help cloning my flat keys
John, since your tags are 125kHz it should be perfectly fine for you for a first start if you simply built a simple diode detector receiver (like in my slides) and try with that. It should enable you to sniff the communication between tag and reader and give you at least a good idea as to what you're dealing with. And, depending on what you find, building an emulator will not be much harder.
Build the sniffer, connect it to the microphone input of a laptop (if you don't have one handy: recording with an audio recorder and later playing back might also work) and hold the receiver next to a door reader. Then use an audio tool (I highly recommend baudline!, set it to at least 48kHz sampling rate) to look at the received signal. You'll either see repeating data bursts or nothing at all. If you see repeating data bursts, that's kind of bad news: this is a more complicated system and you'll probably need a 'proper' emulator to fake a tag. This can be a proxmark, but might just as well be a simple microprocessor (an Arduino, for example) and some circuitry (similar to the original Prox/RFID).
Much more likely you won't see anything. This either means that your sniffer isn't working, or that your door reader is one of the stupid kind (which is suggested by the PDF xeroeffect linked to). Now hold your tag onto the door receiver and you should hopefully see an ever repeating data signal. This is the ID of your tag and all that is needed to open the door (so, don't go and post a recording of it on the internet :).
(Note that I'm a little bit fuzzy on the physics involved here, but I'm reasonably certain that not all sniffer/reader/tag stack combinations will work. I've always had the reader coil laying on top of the sniffer coil, and holding the tag over the reader coil. If yours doesn't work at first, try the other combination.)
To get a better visual idea of what you're supposed to be seeing, watch the start of my talk at HAR2009: http://www.rehash.nl/ (then HAR2009, then Breaking Hitag2). There is one of the stupid ID-only tags right at the beginning (at 03:45 in the recording) followed by a mute tag (only the reader talking) followed by challenge-response tag (reader sends some data, tag sends some data, 05:00 in the recording) and then some more of both types.
What I'm using there is the original sniffer, paired with a commercial Hitag2 reader. This reader will periodically query for Hitag2 tags (which is a kind challenge-response protocol), so that's why you're seeing data bursts even when there is no tag nearby. However, it will also emit a continuous carrier, which is enough to activate stupid, ID-only tags, so that's why it works with both types. (The stupid tags will simply ignore the Hitag2 queries from the reader.)
Offline
#12 2009-08-23 03:06:34
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Well.... i've probibly re-written this post like 8 times.
I read XERO's post, wrote a reply, did some reading, scraped the reply and wrote something else, read some more, re-wrote the post again, read henryk's post, re-wrote it again, did more reading, etc etc...
But this is what i think i'm going to do:
I liked the idea of making a LF diode receiver (mainly because it would be cheap ![]() ), but at the end of the day i'm only partly doing this because i 'need' too. The other reason i'm doing it is because i want to learn more about RFID security.
), but at the end of the day i'm only partly doing this because i 'need' too. The other reason i'm doing it is because i want to learn more about RFID security.
In which case, i think i'm better off getting a job and buying a Proxmark3 from someone who knows more about electronics than i do ![]()
It'll help me out in the future with other RFID projects, and i can dive right in with the programs that comes with it.
So tomorrow morning, ( it's 3:00am now, so i really mean around 11:00 when i wake up -_-; ) i'll pop down to the bank, and see if i can afford to get one today. If i can, it'll probibly arrive in 3/4 days from now, and i'll be able to find out a LOT more about these fobs.
Depending on what i find will determin the next course of action. If it's challange/response, then yeah i'm slightly buggered - but hey, it'll be fun.
You've told me what to look for henryk, and you've helped immensely XERO. Thank you both very much :]
Bye bye sex life ![]()
EDIT:
Also, can someone tell me definitivly whether PM3 works with RFIDiot or not?
It's not in the list of supported hardware - but it seems odd that isn't not - since i imagine PM is the sort of thing every RFID enthusiast keeps on their being at all times..? ![]()
EDIT EDIT:
Also, the HAR 2009 video was really rather impressive Henryk. I can't belive there are carkeys out there which uses plain-text 'authentication'. It's a shame you didn't show a cloned Hitag2 card, or perhaps break a card's encryption earlier, and then read some data off it... but never the less the whole presentation was awesome. I learnt a lot about encryption and cyphers too, so i was really pleased overall ![]()
Makes me want to dump my Genetics degree and switch to Security ![]()
Last edited by John (2009-08-23 15:31:39)
Offline
#13 2009-08-24 04:18:24
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Okay, well, just bought a Proxmark3.
Now you guys will get a bit of peice and quite untill it arrives ![]()
I have another question Henryk - (to add to all the other questions, hehe) - but does Baudline work with the PM3?
The software looks really really useful for analyzing tags in real-time. Perhaps i will be making a diode and cardboard antenna after all -__-;
Offline
#14 2009-08-24 05:44:32
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
I too have a question Henry,
Does windows support Baudline or is it just for linux?
Offline
#15 2009-08-24 14:10:09
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Looking through there website Xero, i don't think they have a Windows port at all:
''Baudline is an X11 based application that runs on Linux and FreeBSD''
You could almost certainly run Ubuntu from a LiveCD in a virtual machine, and do everything from there without even installing anything.
Apparently they ran a comparison between Ubuntu/Fedora/openSUSE, and Ubuntu came out top for speed and font support.
Offline
#16 2009-08-24 15:31:04
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
No PM3 is not supported by RFIDIOt - it wouldn't really make sense to do so as PM3 functionality is all self-contained...
Offline
#17 2009-08-24 16:52:17
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Oh ok - i guess i better read the client manual while the PM is being shipped ![]()
Is there any functionality differences between the Linux/Windows client?
Offline
#18 2009-08-24 21:00:26
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Nope (at least there shouldn't be) - the client is just a front end which allows you to send commands and reports results from the PM3
Offline
#19 2009-08-24 22:52:04
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Awesome, thanks Adam!
Offline
#20 2009-08-25 07:43:41
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
John,
Seeing your doing genetics, are you guys getting any closer to finding a cure for male pattern baldness? Ever since buying this proxmark i'm loosing my hair from scratching my head too much. Any cure?
Offline
#21 2009-08-25 13:20:03
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Hahaha, err. Well i would be suprized if the genes which resulted in male-pattern baldness havn't been identified yet.
If they havn't, i've got a discertation coming up - i can look into it if you like! ![]()
The real problem is that gene therapy - ie, 'curing' people by activating/inactivating genes - is still in it's infancy.
Although there are several ways to go about helping people with genetic disorders, very few of them have passed clinical trials.
So long story short - in five~ten years from now i would be suprized if a whole host of genetic cosmetic products weren't avalible.
Products which altered the genes in hair folical cells, causing perminent hair-colour modification, hair staightness, and rate of hair growth, would all be trivial.
To be honest, cosmetic genetics would be a great thing for me to do my disertation on - seeing as all my male lecturers are bald and aging, and all the female lecturers are... well... female. -_-;
Offline
#22 2009-08-25 20:57:26
- d18c7db
- Contributor
- Registered: 2008-08-19
- Posts: 292
Re: Help cloning my flat keys
Nah, you'd be wasting your time. You need to concentrate on what people want most. Judging by the spam that ends up in my mailbox you need to find the gene that enlarges a certain male member and makes it stay hard then about 80% of the spam trying to sell pills and enlargers would just become obsolete. You'd be a hero to all!
Offline
#23 2009-08-25 21:17:55
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
lol! - you'd just end up with spam for 'gene pills' which will apparently make your penis bigger, heheh.
To be honest, i don't know how you can make things grow with genes after development has taken place...
I could probibly give all your children freakishly large genitalia... something to do with sticking a localised promoter before the FGF gene (hey, if it makes all your other limbs grow..)
But after development is tricky. I'd probibly end up giving your 'special place' cancer ![]()
Offline
#24 2009-09-01 16:25:10
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Whoo hoo!
I just received my Proxmark3 from proxmark3.com!
The shipping was a bit of a pain, because they used USPS to ship (which means after it goes through customs, it is handled by ParcelForce (Royal Mail's parcel division), who are s**t. I had to go to the depo to pay the import duty, and there phone system is a joke.
Anywhoo's, the package it's self contained a LF antenna which looks very sturdy and durable (if not a little ghetto),
a USB to mini USB cable, and of course, a proxmark3 flashed with the latest firmware ![]()
So now i just have to find to tools for the proxmark, and i can start taking a look at my RFID fobs! Whoo!
Offline
#25 2009-09-01 17:33:21
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Hm.
I've tried compiling the source code from ProxSpace.2008.11.11 and ProxSpace.2009.08.26, and i get the error 'The system cannot execute the specified program' for both.
I'll try using the SVN next - but i'm not holding out much hope. There's clearly something i'm missing.
EDIT:
I'm trying to compile on a fully-up-to-date Windows XP install, using these instructions:
http://code.google.com/p/proxmark3/wiki/Compiling
EDIT EDIT:
Getting the .NET frameworks (all of them) seemed to allow me to compile the 2009.08.26 ProxSpace!
Time to flash and run stuff! ![]()
EDIT EDIT EDIT:
After running:
prox load ..\armsrc\obj\osimage.s19
in 0setpath.bat's window, i got:
'Need filename.'
I found if i gave full pathnames for both prox.exe and osimage.s19, it worked! ![]()
Last edited by John (2009-09-01 18:07:16)
Offline
#26 2009-09-01 19:05:05
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Okay, well after a bit of tinkering, i've figured out how to power/listen to the tag.
Tune confirms that it is a 125Khz and not anything else.
Below are screenshots of my losamples, at three different levels of zoom:
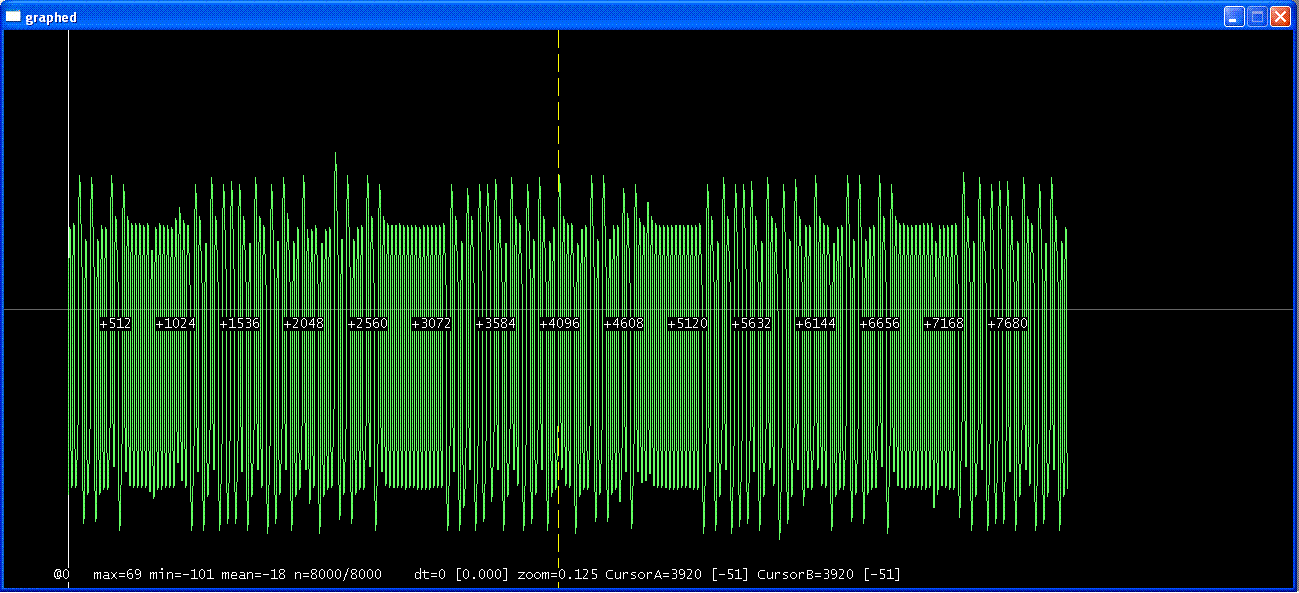
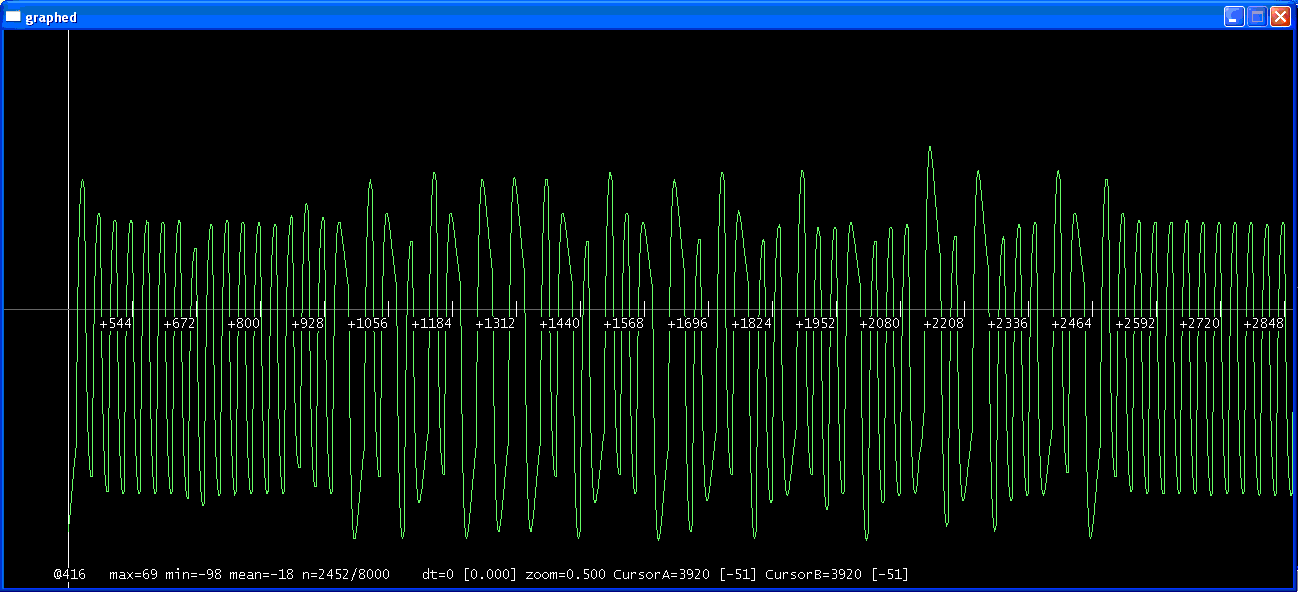
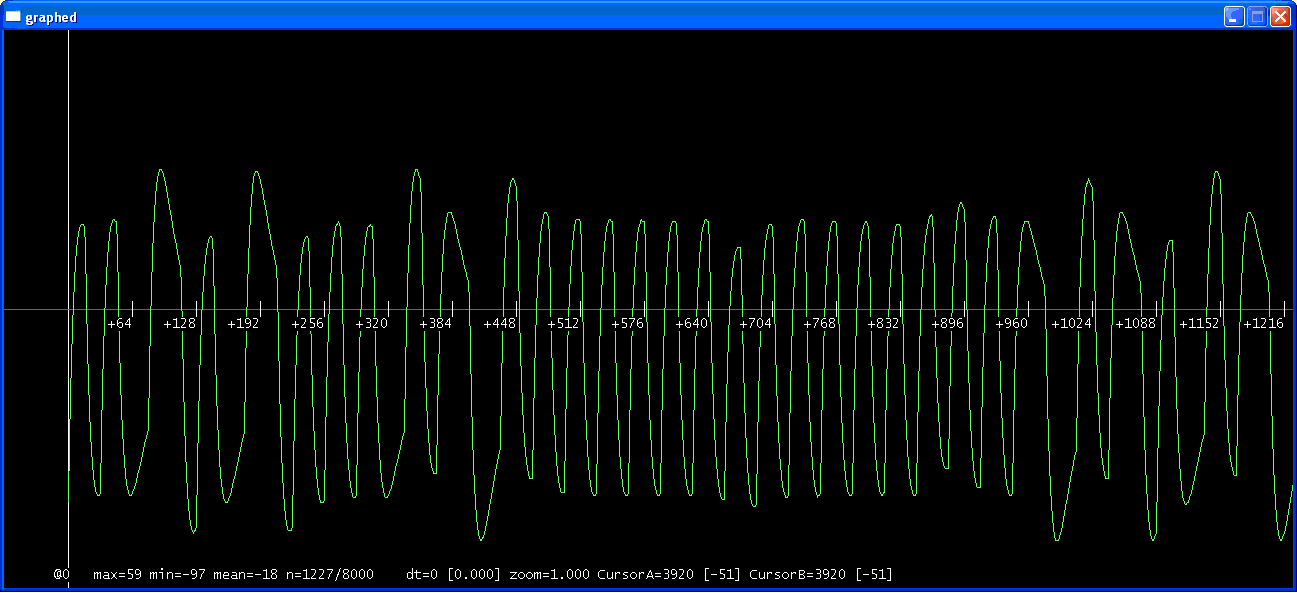
As you can see, it definatly looks (to me) like a repeating signal.
The long bit of (i think) 16 repeating waves must be some sort of refrence point for the reader.
On the back of this RFID tag it says '99531670'
All i've got to figure out now is how the waveform makes that UID, and then how to program another tag to replay that UID.
I also thought - it wouldn't be too hard to make a bruteforcer for a device like this. You know, try all UIDs sequentially untill the proxmark's button is pressed. Or even a fuzzer perhaps, where you put in which bits of the waveform you want to keep static, and highlight which bits you want to 'fuzz'.
Anyway - i love my Proxmark, even though i'm totally unqualified to use it. All i need now is a hard-case to put it in ![]()
Thanks in advance to anyone who reads/comments on this!! ![]()
Offline
#27 2009-09-01 19:21:40
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Send me the samples as a file and I'll have a play. It looks pretty straightforward.
Last edited by adam@algroup.co.uk (2009-09-01 19:21:55)
Offline
#28 2009-09-01 21:13:40
- henryk
- Contributor
- Registered: 2009-07-27
- Posts: 99
Re: Help cloning my flat keys
John, this looks like for cloning you'd get away with simply askdemod, then losim like Jonathan did in his original Verichip cloning: http://cq.cx/verichip.pl
(Also, his signal looks remarkably close to yours.)
Offline
#29 2009-09-01 21:15:28
- d18c7db
- Contributor
- Registered: 2008-08-19
- Posts: 292
Re: Help cloning my flat keys
Yes, save the samples file then upload it to the files section of the forum then we can have a play with it.
Offline
#30 2009-09-02 00:01:33
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Wow, thanks guys! Seriously, thank you so much for the support! :3
Here's the samples i sent to Adam earlier:
http://www.proxmark.org/files/index.php … sit999.pm3
Erm, i'm going to have a look at that site Henryk, and see if i can figure out how to demodulate this waveform using the method described.
...I've learnt a lot today. Thanks guys :]
Offline
#31 2009-09-02 00:16:04
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
The problem with askdemod is it expects a nice clean sample where all the peaks reach MAX/MIN, like this one:
but what we've got is this:
which has two problems... Firstly, the peaks don't hit MAX/MIN, and secondly, if you look closely at the lower halves of the samples, you'll see false peaks within the main peak...
we can get rid of the second problem by using the 'dec' (decimate) command (in this case, repeat it three times):
and we can get rid of the first problem by amplifying the signal (I have added a new command to do this - 'amp'):
and we can now run askdemod:
Offline
#32 2009-09-02 00:30:49
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
I hope you don't hate me for this, but.. hehe... i diliberatly held the tag a few Cm's away from the reader to get a 'prettier' graph.
I figured if it was reaching max/min, it would be missing information which might be important. I couldn't have been more wrong eh? ![]()
But it's great to learn how you would do it when the signal isn't reaching max/min! Thank you!
I'll grab another sample now at better quality. Sorry guys -_-;
EDIT:
Here is it ![]()
http://www.proxmark.org/files/index.php … better.pm3
EDIT EDIT:
Actually, forget that, that was a terrible sample. This one is even better (if you want lots of mins/max's)
http://www.proxmark.org/files/index.php … 9-best.pm3
Sorry for flooding the uploads dir with samples!
Last edited by John (2009-09-02 00:53:58)
Offline
#33 2009-09-02 11:41:59
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Well, that's loads better! now you can simply manchester decode it:
proxmark3> mandemod 32
> mandemod 32
Manchester decoded bitstream
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
which produces an interesting effect... Note that the 12th and 13th bits are always '11'?
Anyway, this would suggest that the baseband encoding is the same as an FDX-B tag, even if the data is layed out differently, and is therefore eminently clonable since the data is basically these 64 bits repeated:
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1
If you ping me off-forum with your snailmail address I'll program a Q5 and send it to you so you can test it out...
Offline
#34 2009-09-02 12:25:56
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
Adam,
How would you go about programming a Q5 card with the 64 bits you mentioned above?
I mean, would you somehow convert those bits to hex?
Thanks.
Last edited by XEROEFFECT (2009-09-02 12:27:20)
Offline
#35 2009-09-02 12:28:18
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
OK, so I've programmed a Q5 and re-read it with the PM3, and to get the right output I needed to change the FDX-B standard scheme from biphase encoding with inverted output 128 bits to manchester encoding, non-inverted output and 64 bits. My readout now looks like this:
proxmark3> loread
> loread
#db# 00000000, 00000026, 00000000
proxmark3> losamples 4000
> losamples 4000
proxmark3> mandemod 32
> mandemod 32
Manchester decoded bitstream
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
1 0 1 1 0 0 1 1 0 1 0 1 0 1 1 0
0 1 1 1 0 1 0 0 1 1 0 0 0 1 1 1
1 0 0 0 0 1 0 0 1 0 0 0 0 1 1 0
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1
which is identical data with a slightly different offset so it looks like we're good to go... ![]()
Offline
#36 2009-09-02 12:30:08
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Xeroeffect - yes, if you look at the fdxbnum.py code in the RFIDIOt distribution, you'll see how this is done. Once John has tested my clone I'll update the distro with a 'transit.py' program for doing these.
Basically, you set a control parameter that tells the Q5 what modulation scheme to use, how many bits to send etc., then you program it's data blocks with the bit pattern you want to send and you're done!
Last edited by adam@algroup.co.uk (2009-09-02 12:31:36)
Offline
#37 2009-09-02 13:40:08
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
This is similar to what I am trying to do. The only difference is that Johns tag uses ASK modulation and my tag (Keri.pm3) uses FSK. So theoretically speaking, I could follow the same procedure described above and Program the bits along with the FSK modulation to the Q5 tag. Is that possible?
Edit
But then again, I remember d18 telling me that my tag wasn't Manchester encoded on another topic post 5 ![]()
Last edited by XEROEFFECT (2009-09-02 14:18:36)
Offline
#38 2009-09-02 14:27:01
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Q5 supports FSK mode, so yes, in theory it's possible.
Offline
#39 2009-09-02 14:39:13
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
Thanks Adam. You've been great help. I'll just have to play around with the Q5 tags. It'll be a case of hit and miss till I get it right. Fingers x'd.
Offline
#40 2009-09-02 14:42:40
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Hey hey! Very nice work Adam!
I just did another loread/losaples/mandemod 32 on the same card, and i got exactly the same output as you Adam, except my offest was slightly different.
I'm fairly sure which steps you performed to know the period/samples to know to run mandemod 32. I'm not exactly sure how you knew it was manchester encoded and not ASK/FSK, but i'm sure i'll figure it out.
I'll send you my address now Adam - thank you so much for your help. It's really too kind!
And thank you XERO and Henry - you have both helped me immensely!!
I'll try and figure out after i grab some lunch how that translates into the code on the back.
I also scanned a Transit 500, one of the smaller key tags, for comparison.
I figured i could deduce from a second tag which parts are static, and which parts are variable.
Unfortunatly, the whole thing was different... as show below:
0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 1
0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0
0 0 0 1 1 0 0 1 0 0 1 0 1 1 1 0
1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 0
I've got a second Transit 500 (a flat mate has it, and she's currently out) - and i'm sure other residents of my building will let me read their Transit999 for comparison.
Again, everyone - thank you!
(And i'll try and help you XERO anyway i can!)
Offline
#41 2009-09-02 15:02:43
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Working out the pulse width is easy. Just lay a grid over it until you find one that fits (you can also do some maths if you know how many bits your dealing with etc., but since we don't it's simpler to do it visually):
Use the left and right keys (and 'ltrim 1') to get the data to line up with the grid in such a way that the large pulses take up a whole grid section and the small pulses divide it in two. If this works, then you've got standard Manchester encoded data. If not, then the modulation is some other scheme.
Offline
#42 2009-09-03 02:45:42
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
Hey John, Im so happy it all worked out for you ![]() you can now officially consider your proxmark an investment. I can imagine the adrenaline rush as soon as you receive your package and make your way to the reader...... it feels so good! Hopefully I'll get my hit soon enough.
you can now officially consider your proxmark an investment. I can imagine the adrenaline rush as soon as you receive your package and make your way to the reader...... it feels so good! Hopefully I'll get my hit soon enough.
Offline
#43 2009-09-03 03:05:13
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Ah, that's a much better way than the math-based way i was previously doing it! Thanks Adam!
I've been reading/demodding all the tags i can get my hands on today (well, three...) and after spending a long time playing with the binary, i've finally figured out how the ID on the back of the tag relates to it.
Unfortunatly, i don't think you will like the news... depending on what the news means.
The three fobs i scanned gave me the following mandemod:
Transit 999 [ID = 99531670]:
1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0
1 1 0 0 1 1 0 1 0 1 0 1 1 0 0 1
1 1 0 1 0 0 1 1 0 0 0 1 1 1 1 0
0 0 0 1 0 0 1 0 0 0 0 1 1 0 1 1Transit 500 [ID = 04008064]:
0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 1
0 0 0 0 0 0 0 0 0 0 1 0 0 0 0 0
0 0 0 1 1 0 0 1 0 0 1 0 1 1 1 0
1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 0 Transit 500 [ID = 05015749]:
0 0 1 0 1 0 0 0 0 0 0 0 1 0 1 0
1 0 1 1 1 0 1 0 0 1 0 0 1 0 1 0
0 0 0 0 0 1 1 1 1 0 0 1 0 0 0 0
0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0Using the two Transit 500's code, a lot of staring, and a lot of patience, (i'm a little bit stupid, i could have just made it into one big line and searched for it straight away. Instead, i was messed about by the off-set) i finally figured out that the ID is 4 bit binary (totalling 32 bits) and there's a 32 more bits which seems to be like a static string, and perhaps some checksum string as well (i can't tell where the static ends exactly, as the variable bit might be the same by chance).
So basically i ended up with this:
0 0 0 0 - 0
0 1 0 0 - 4
0 0 0 0 - 0
0 0 0 0 - 0
1 0 0 0 - 8
0 0 0 0 - 0
0 1 1 0 - 6
0 1 0 0 - 4
1 0 1 1 1 0 1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 00 0 0 0 - 0
0 1 0 1 - 5
0 0 0 0 - 0
0 0 0 1 - 1
0 1 0 1 - 5
0 1 1 1 - 7
0 1 0 0 - 4
1 0 0 1 - 9
0 1 0 0 0 0 0 0 1 1 1 1 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0Some of that last 32 bit looks static - but it's hard to tell where it ends with just two tags.
The interesting bit (for me at least) is what happened when i looked for the ID with the Transit999 (the one Adam made a clone of)
I couldn't find the ID at all - however, there was a long series of '1's
This made me think that perhaps the code was the inverse of the correct code - and, whaddya know - it was.
1 0 0 1 - 9
1 0 0 1 - 9
0 1 0 1 - 5
0 0 1 1 - 3
0 0 0 1 - 1
0 1 1 0 - 6
0 1 1 1 - 7
0 0 0 0 - 0
1 1 1 1 0 1 1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0I have no idea why...
Perhaps the Transit 999's bitstream is just inverted,
Perhaps i read the fob with the proxmark antenna upside down/backwards? (Would this have this effect?)
If it's the former, then hopefully Adam's clone will work, as the reader will accept both.
If my antenna has a back and a front... well... i guess that means Adam's clone won't work -_-;
Anyway - i hope this thread proves to be useful for someone doing something similar with 'stupid' keyless access systems.
The next step is figuring out what the non-static parts of the 32bit string is, as well as how it's made (so i can just look at the ID on the back of someone who wants a cloned fob, and using there ID alone make a perfect 64bit clone)
Then finally, figure out how to program a Q5 the same way as Adam did ![]()
It would also be a fun side-project to figure out how, using just the 64bit code, to program the proxmark to act as a tag (just like a Q5).
Then i could set IDs such as 00000000, 99999999, 12345678, etc, to see if the vendor added any naughty backdoors.
Perhaps even make the proxmark bruteforce the reader by starting at 00000000, and go upwards untill the button is pressed, and then printing the last ID used to prox.exe
Perhaps i'm getting a little too ambitious, hehe, but none the less - i'm quite clearly enjoying learning more about RFID with you guys ![]()
EDIT:
I just saw your message XERO ( i took a while writing this post ![]() ) and i know what you mean.
) and i know what you mean.
I was using calc to get the binary from the ID numbers, and i was like "0110... okay....1001.... okay great, that's two in a row...this is looking good........ 0010! That's three in a row! YESSSSSS! 0001, bam, 0100, bam, 0000, yes! Bingo! They all match up! I've got it!"
Then when i did it for the inverted bitstream... whoo. It's ridicuously geeky, but there was definatly a rush of adrenaline when i realised i was right ![]()
Anyway - after all this we've got to get your fob's cloned XERO ![]()
Last edited by John (2009-09-03 03:10:45)
Offline
#44 2009-09-03 05:14:10
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
If these readers are standalone i.e not hooked up to server -which I firmly believe they are- then there is definately the chance you could find the backdoor and even program new cards to it. Well done John, You finally defeated the evil encryptor! Welcome to the Matrix, now you'll have to choose your pill. Choose it wisely, there's no turning back.


I've Already tried the red one- Makes your hair fall out.
Last edited by XEROEFFECT (2009-09-03 05:37:25)
Offline
#45 2009-09-03 09:08:23
- adam@algroup.co.uk
- Contributor
- From: UK
- Registered: 2009-05-01
- Posts: 203
- Website
Re: Help cloning my flat keys
Good work on the decoding John!
No, the antenna isn't going to make any difference - the data will be whatever it is, and it's quite common for TAG data formats to vary even when they are from the same manufacturer, so the inversion is not an issue. I'll take a look at it to see if I can figure out checksums etc.
As far as emulation goes, that really shouldn't be a problem. The PM3 is quite capable of emulating this tag.
I was also thinking about adding the programming functionality so we can use the PM3 to program Q5 tags. Now that Henryk has added bidrectional support for LF tags this shouldnot be difficult (actually, I'm not sure that's needed, but just in case it is... ). Again, I'll take a look.
In the meantime, the way I programmed the one I sent you was with an ACG LF reader and a modified version of fdxbnum.py. I'll need to add the code to convert from the printed number to the bitstream before I release it though, so we may be in for some further testing...
Offline
#46 2009-09-03 09:31:28
- henryk
- Contributor
- Registered: 2009-07-27
- Posts: 99
Re: Help cloning my flat keys
Working out the pulse width is easy. Just lay a grid over it
You probably don't even need the grid. Recognizing Manchester encoding is pretty straightforward by just looking at the waveform: If there are only two types of time durations for the high and low states --short and long, where long is twice the time of short--, it is practically guaranteed to be Manchester or Biphase (both look the same on the wire/air). The bit period is simply the 'long' time, or twice the 'short' time.
I was also thinking about adding the programming functionality so we can use the PM3 to program Q5 tags. Now that Henryk has added bidrectional support for LF tags this shouldnot be difficult (actually, I'm not sure that's needed, but just in case it is... ).
Note that my additions relate to emulating tags, not emulating a reader. LF reader emulation should have been working before with the locomread command, at least for simple pule-width based readers (like Hitag2). I couldn't get it to work straight away when I was trying (at HAR, on the night before my talk) but I guess that just takes some parameter tuning next time I'm near an oscilloscope.
I do think we need a more structured, framework-y approach to these things though. The current code is an exquisite mess of several highly specific functions and a few halfheartedly generalized functions (e.g. why is that parameter "BOOL at134khz", why is it not "int divisor"?). There are only a couple basic functionalities (passively sniff, emulate tag, emulate reader) with only a few modulations and encodings, so that it shouldn't be too hard to get everything together. Just last weekend I found myself at a youth hostel with a very peculiar RFID door lock (like TI tags, e.g. power first, then listen, but with a couple of bits communication from reader to tag before the listen mode) and there wasn't any simple LF sniffer code. (And I forgot to bring my diode detector receiver.) I stringed something together with modified FPGA code, but needs quite some refactoring to be useful in general.
Offline
#47 2009-09-03 13:29:06
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
I agree, the software / firmware /documentation for the Proxmark3 is not exactly user-friendly..
For example, the description of the losim command in the refrence manual (here) for example, doesn't fully explain how to use it. Does it use the data from whatever the last *demod function is? Can it be given arguments such as bitstream/modulation type? Could it be modified to support ranges (for bruteforcing)?
Don't get me wrong - as is, the proxmark is still immensly useful.
All i'm saying is that with a bit more.. erm.. co-ordination, it could be the only device anyone would need when discovering / testing / simulating ALL RFID tags.
But hey - i don't code in whatever language you guys use for the prox.exe software or VHDL (i presume) for the FPGA - so i have no idea how hard it must be to be a developer of the PM3! For all i know, just organizing all the existing code into a most-feature-rich-firmware-package-ever could take a year! It's not my place to go on about it when i'm no capable of doing anything about it myself ![]()
I'm glad to hear Adam that there's a good chance that you cloned card may still work! I'm dead excited about checking the mail every day now ![]()
The ACG LF reader you mentioned... I've looked all over the internet for it, but it seems that ACG have become part of HID and their Omnikey range.
I did find a site selling a LF/HF ACG card here. Is this the one you have that works with your code?
The upsetting thing is, i bet the PM3 is potentially capable of doing everything that the ACG device does. hehe ![]()
Anyway, i'll go back to trying to figure out the checksum/parity - I took the red pill as soon as i put down a large proportion of my student loan on a Proxmark ![]()
Offline
#48 2009-09-03 13:45:40
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
John,
If your interested in one of the ACG readers, Adam sells them on his RFIDIOt site.
Last edited by XEROEFFECT (2009-09-03 13:47:02)
Offline
#49 2009-09-03 14:19:46
- John
- Contributor
- From: Wales
- Registered: 2009-08-21
- Posts: 56
Re: Help cloning my flat keys
Oooh, ouch.
Either £395 for the HF & LF one, or £140 for the LF one.
This is tough...urgh... on the one hand, it would be awesome to have a HF/LF reader.
On the other, it's £395!!!! :'(
That would make a total of like £700 spent on RFID equpiment in around a week >_<
That's almost 350 pints from the student union >_<
That's 525 Units of alcohol!
Based on my weight, that's enough to kill me almost 30x over! What a waste ![]()
If i get the LF only one, i'll save £255.... but i'll forever be wishing i got the one that did HF's as well.
Well at least i'll have the cash to drink my sorrows away...
Okay, it's settled, i'll buy the LF only one and a few crates of alcohol to soften the blow.
First i have to inform the misses, take shelter, and once she's cooled down ask her for my wallet -_-;
EDIT:
Wait a sec XERO - is that Adam 'Adam', as in the Adam from here !?
Dude. This thread is full of celebrities. O_O
Henryk, d18c7db, and now the guy who runs RFIDiot.... i got seriously lucky when i registered here didn't i -_-;
Last edited by John (2009-09-03 14:27:16)
Offline
#50 2009-09-03 14:33:10
- XEROEFFECT
- Contributor
- From: Sydney Australia
- Registered: 2009-07-20
- Posts: 132
Re: Help cloning my flat keys
@ John
Hahaha.... She'll probably kill you but then again, whatever she dosn't know wont hurt her ![]() . Just pretend you spent it on a really cheap Genetic Analyser you found on a really cool site you accidently stumbled across one really late night while you were up trying to finish a really hard assignment. Whatever you do don't let her know. It's gonna come back and bite you in the ass.
. Just pretend you spent it on a really cheap Genetic Analyser you found on a really cool site you accidently stumbled across one really late night while you were up trying to finish a really hard assignment. Whatever you do don't let her know. It's gonna come back and bite you in the ass.
Edit:
I just saw your edit and I'm laughing hysterically. Yes- The guy that helped you runs the site. Quick- delete your last post or you won't get your tag. ![]() Oh by the way, make sure you ask Adam to sign it for you.
Oh by the way, make sure you ask Adam to sign it for you.
Last edited by XEROEFFECT (2009-09-03 14:46:06)
Offline